A report of an Apple GPU security flaw has been confirmed by the company, acknowledging that the iPhone 12 and M2 MacBook Air are affected.
An exploit has been demonstrated by security researchers, which would allow an attacker to view data processed by the chip, including the results of things like ChatGPT queries …
ADVERTISEMENT
What is the Apple GPU security flaw?
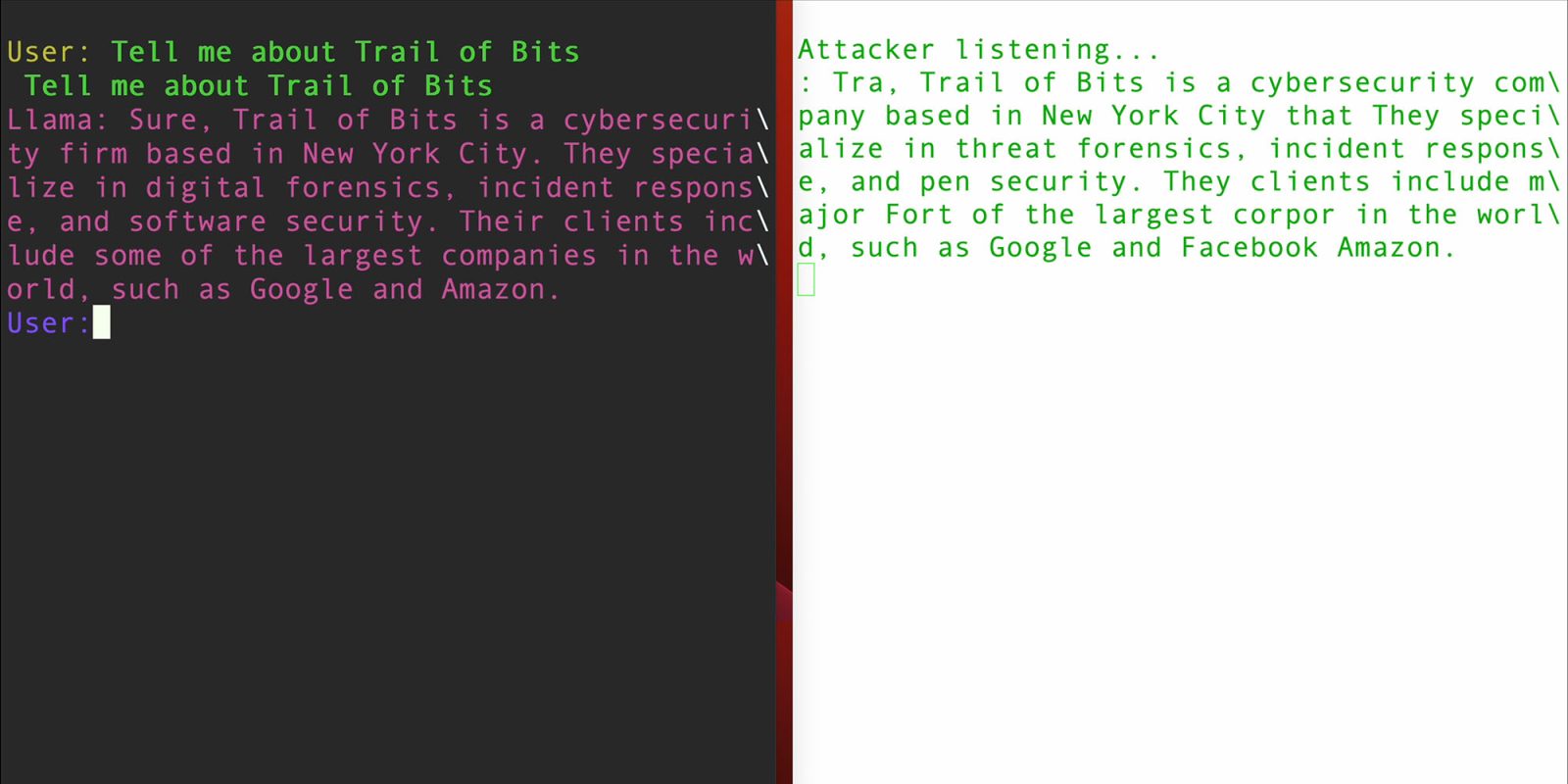
Security researchers at Trail of Bits have discovered a vulnerability in a number of graphic processor units (GPUs) made by Apple, Qualcomm, AMD, and Imagination. They’ve named the flaw LeftoverLocals.
They’ve demonstrated an exploit where an attacker who has local access to the device can read data in the GPU which was left over from earlier processing, hence the name. The proof of concept allowed them to accurately read the results of an AI chatbot query.
Which Apple devices are affected?
The complete list is unknown at this point. The researchers reported their findings to Apple and other affected companies, giving them time to issue security patches before the vulnerability was made public.
Trail of Bits say that Apple patches some devices, including those running on the A17 and M3 chips, but others remain vulnerable.
We re-tested the vulnerability on January 10 where it appears that some devices have been patched, i.e., Apple iPad Air 3rd G (A12). However, the issue still appears to be present on the Apple MacBook Air (M2). Furthermore, the recently released Apple iPhone 15 does not appear to be impacted as previous versions have been. Apple has confirmed that the A17 and M3 series processors contain fixes, but we have not been notified of the specific patches deployed across their devices.
Apple has confirmed that both the iPhone 12 and M2 MacBook can still be successfully attacked. Wired says that other Apple devices may remain vulnerable.
An Apple spokesperson acknowledged LeftoverLocals and noted that the company shipped fixes with its latest M3 and A17 processors, which it unveiled at the end of 2023. This means that the vulnerability is seemingly still present in millions of existing iPhones, iPads, and MacBooks that depend on previous generations of Apple silicon.
How serious is this?
The exploit demonstrated needs some kind of existing access to the machine, meaning it falls into a low risk category at present.
The concern, as Wired notes, is whether it could be chained with other forms of attack.
Though exploiting the vulnerability would require some amount of existing access to targets’ devices, the potential implications are significant given that it is common for highly motivated attackers to carry out hacks by chaining multiple vulnerabilities together. Furthermore, establishing “initial access” to a device is already necessary for many common types of digital attacks.
What should you do?
As always, keep your devices updated with the latest supported OS versions.
FTC: We use income earning auto affiliate links. More.
ADVERTISEMENT
